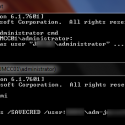
On a Dell server I needed to determine the physical hard drive location for a faulty disk. Within the operating system the disk was mounted as /dev/sdk so I ran: udevadm info –query=all –name=/dev/sdk And from the output I could correlate this with the information in the iDRAC: So in this example disk 10 on… Read more »
Posts Categorized: linux
Dell racadm on Linux
I’m currently using Linux Mint and wanted to communicate with the iDRAC interfaces on Dell servers. Install racadm: sudo echo ‘deb http://linux.dell.com/repo/community/ubuntu xenial openmanage’ | sudo tee -a /etc/apt/sources.list.d/linux.dell.com.sources.list sudo gpg –keyserver pool.sks-keyservers.net –recv-key 1285491434D8786F gpg -a –export 1285491434D8786F | sudo apt-key add – sudo apt-get update sudo apt-get install srvadmin-idracadm8 Test with: /bin/racadm -R… Read more »
Command Line Optimise JPEG image
This command significantly improved file size on disk although the quality value can be increased to adjust the image quality versus file size: convert input-file.jpeg -sampling-factor 4:2:0 -strip -quality 60 -interlace JPEG -colorspace RGB output-file-60.jpeg
Apache: unable to open logs
In the annals of “Everyday is a learning day”. I have an Apache server hosting student websites, and the number of websites grew to over 700 within a day and Apache was complaining with error: unable to open logs It took a little while to narrow down the problem as I assumed there was a… Read more »
Locating Excessive Inode Usage
The command to list the directories using the most inodes is: find . -printf “%h\n” | cut -d/ -f-2 | sort | uniq -c | sort -rn However, I first needed to narrow down the directory under root that might be causing the problem: df -i showed that the root directory (/) was the problem…. Read more »
Configure Java Security Settings on Linux
I received the following error message when trying to run a Java JNLP file: Application Blocked by Security Settings Your security settings have blocked a self-signed application from running Assuming I trust the program I found I could get it to run by amending the Java Security Policy: Amending the Java Security Policy The first… Read more »
Intel Xeon Phi Co-Processor Setup

Introduction Just adding my notes here in case it helps anyone else who finds themselves in a similar situation to me.I have two machines each with an Intel Xeon Phi Co-Processor board. This (in my basic view of the world) is like an extra machine inside the host machine but contains 240 processors clocking in… Read more »
Selectively Checking Disk Usage Excluding Files and Folders
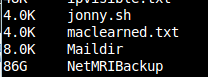
Normally to check the disk usage of directories on a linux system I would run: du -sh * However, occasionally I want to exclude particular directories that take a long time to check and/or that I am not interested in anyway. The example below run from the root of the filesystem skips checks for /home… Read more »
Fido U2F Security Key

So I ordered a FIDO U2F Security Key from a French company ‘Plug-Up’ to have a little play. It is used in 2-factor authentication so when logging in to a service you first enter your username and password and if correct your are prompted for your second factor (a code sent by SMS or a… Read more »
Linux GPS Logging Data
I took part in a swim this weekend – The Battle of Carlingford Lough. My friend Cormac gave his Panasonic Lumix camera to Mary in the kayak and set the camera to log GPS data. He sent me the GPS log file and I opened the log file with BT747 – a Java application that… Read more »