Hashicorp Vault supports several backends for secret storage. I was creating a test Vault to play with PKI certificate generation and started with installing Zookeeper
After download the Vault binary and extracting it to /usr/local/sbin/vault, I created a config file at /etc/vault/config.hcl
vi /etc/vault/config.hcl
storage "zookeeper" {
address = "127.0.0.1:2181"
path = "vault/"
}
listener "tcp" {
address = "0.0.0.0:8200"
tls_disable = 1
}
api_addr = "http://0.0.0.0:8200"
ui = true
I then ran vault in a screen session with:
vault server -config=/etc/vault/config.hcl
The next step was to initialise Vault with the new backend:
export VAULT_ADDR='http://127.0.0.1:8200'
vault operator init
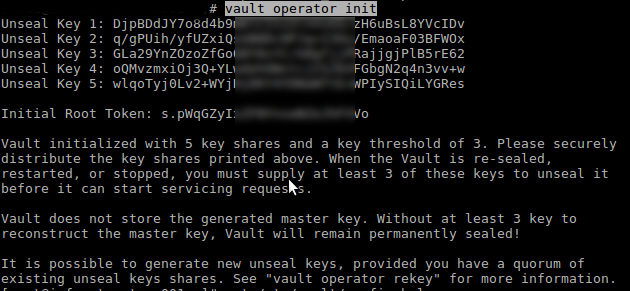
The ‘init’ command provides the keys needed for unsealing the vault and in a real environment these would need to be kept safe and with different users/machines.
With the keys provided the next step is to unseal/unlock the vault using the following command multiple times with the unseal keys until the ‘Sealed’ status returns ‘false’ :
vault operator unseal
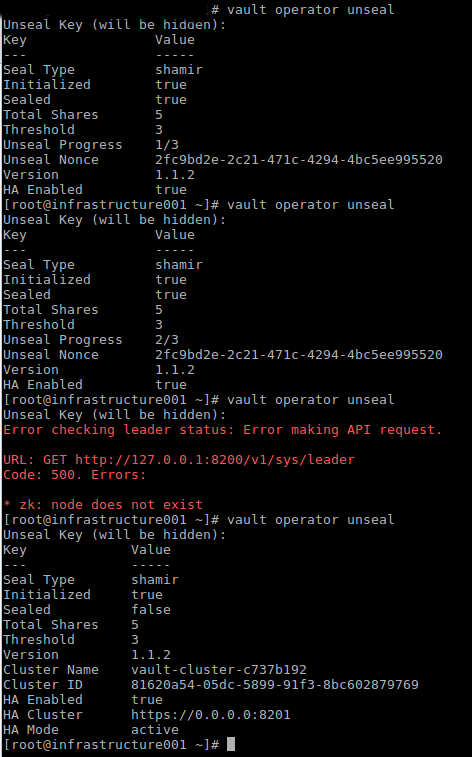
With the vault unsealed login using the root token provided after the init command above:
vault login <token>
Or set it in an environment variable:
export VAULT_DEV_ROOT_TOKEN_ID="s.XmpNPoi9sRhYtdKHDELETEME"
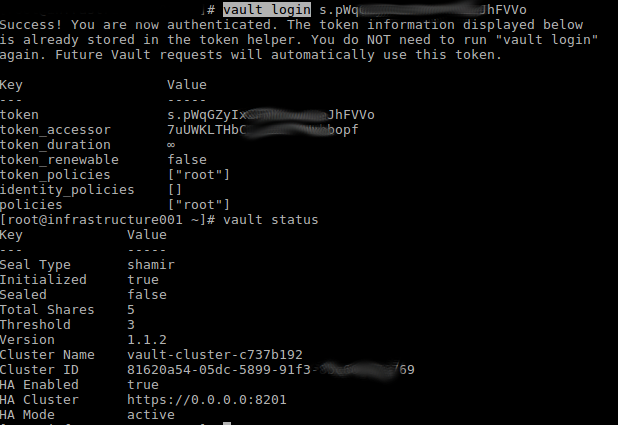
Normal vault commands such as those below should work fine now:
vault status
vault secrets enable -path=dev kv
vault write dev/influx dbpass="topsecret"
vault read dev/influx
echo $(vault read dev/influx | grep dbpass | awk '{print $2}')
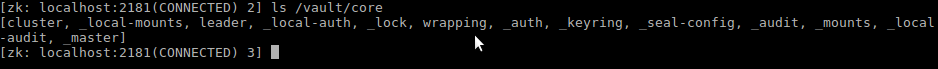
If the Vault service is stopped the unseal keys will be needed again to get it unlocked. Also logging in to Zookeeper (/opt/zookeeper/bin/zkCli.sh) shows nodes under the /vault path: