For a new vault cluster, add the APT repo:
curl -fsSL https://apt.releases.hashicorp.com/gpg | sudo apt-key add -
sudo apt-add-repository "deb [arch=amd64] https://apt.releases.hashicorp.com $(lsb_release -cs) main"
sudo apt-get update && sudo apt-get install vaultDepending on how you have configured the listener you may need to set an environment variable specifying the vault location before commands like ‘vault status’ will work:
export VAULT_ADDR=https://192.168.1.91:8200
export VAULT_SKIP_VERIFY=trueNotice I am setting a variable to disable certificate verification to avoid having to add ‘-tls-skip-verify’ to each command. This is only set as I am using a self-signed certificate. If you are using a globally recognised certificate you could omit this parameter.
After installing you need to run the vault server in one terminal and in another terminal initialise the new vault and keep a record of the keys used to seal and unseal the vault.
vault server -config /etc/vault.d/vault.hclthen initialise:
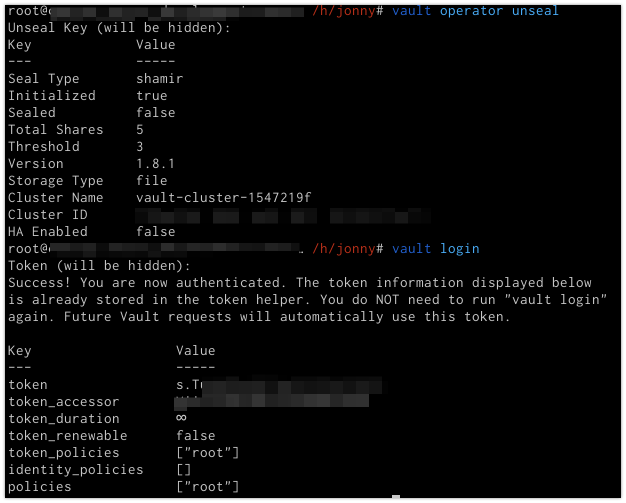
vault operator initMake sure to store the unseal keys in safe places.
You can check the status of the vault with:
vault statusExample status output:
Key Value --- ----- Seal Type shamir Initialized false Sealed true Total Shares 0 Threshold 0 Unseal Progress 0/0 Unseal Nonce n/a Version 1.8.0 Storage Type file HA Enabled false
Unlock the vault
vault operator unsealYou will need to run the above command 3 times providing unseal keys each time. When the vault is unsealed you will need to login against the vault to begin adding items.
vault loginAt the prompt enter the ‘Initial Root Token’ value generated in the ‘vault operator init’ step. Alternatively it can be added as an env var:
export VAULT_TOKEN="s.XmpNPoi9sREDACTEDx"Enable Github Authentication for Users
vault auth enable githubThen write as shown below with the organisation name as used on Github:
vault write auth/github/config organization=mygithuborgnameSpecify a policy for particular teams if desired:
vault write auth/github/map/teams/engineering value=developerThen on another terminal login using a Github API token:
vault login -method=github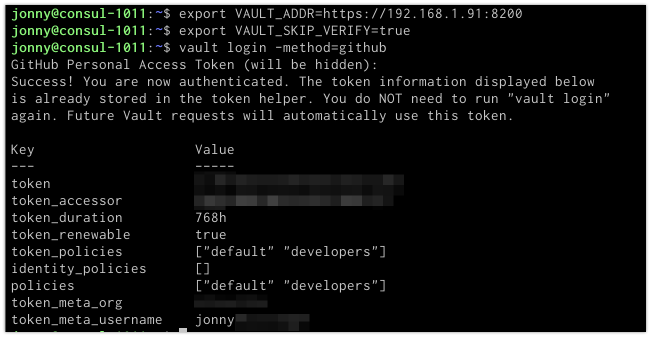
Policies
We want to allow developers to read and write secrets under a path named ‘secret’. So first enable the key-value secrets engine for the path ‘secret’
vault secrets enable -path=secret kvThen create a policy for developers that allows creating secrets under that path:
vault policy write developers - << EOF
path "secret/*" { capabilities = ["create", "update", "read"]}
EOFThen save a secret:
vault kv put secret/dbpassword value=opensesameand to retrieve it:
vault kv get secret/dbpassword Service Management
With Vault installed you can manage the service like any other with ‘systemctl’:
systemctl enable vault
systemctl start vaultStorage Engine Config
The config file at /etc/vault.d/vault.hcl is used to set the storage backend to use vault or the filesystem:
ui = true
storage "consul" {
address = "127.0.0.1:8500"
path = "vault"
}
# HTTPS listener
listener "tcp" {
address = "0.0.0.0:8200"
tls_cert_file = "/opt/vault/tls/tls.crt"
tls_key_file = "/opt/vault/tls/tls.key"
}Web UI
You can visit the web UI on port 8200 if you have enabled it in your config. You will need to login with the root ‘Initial Root Token’ value generated in the ‘vault operator init’ step.